Expert Cybersecurity Leadership, On Demand
In this age of unprecedented levels of cyberattack, the CISO is the captain of your cybersecurity ship. Security can no longer be driven by IT alone.”
Rich Dussliere, Office of the CISO and vCISO
Every Organization Needs a CISO
Every organization requires a Chief Information Security Officer to lead initiatives in cybersecurity, privacy, and data protection. But not every organization has the talent or resources to ensure a full-time on-premises CISO. This doesn’t mean that you need to remain vulnerable to cyberthreats, phishing scams, ransomware, and all the other dangers on the digital landscape.
Fractional CISO Service by iShift
- Our vCISO service is designed to help mitigate risk and vulnerabilities, align your team in cybersecurity and compliance, and strengthen your organization’s overall security posture.
- We are offering CISO-level expertise to organizations from regulated industries that lack the resources or talent for a full-time CISO.
- Our service is powered by iCompli, an AI-enabled vCISO platform designed to deliver structured process and predictable outcomes.

What a vCISO Does
Evaluate
Connects the organization’s goals to security risks
Design
Creates a viable security strategy tied to the company objectives
Identify
Uncovers cybersecurity gaps and understands strategic vulnerabilities
Supervise
Oversees compliance processes relevant to the industry
Mitigate
Implements remediation plan to address cyberthreats
Educate
Updates stake-holders of imminent digital risks
Inform
Reports to top management in a meaningful way
vCISO Benefits for Your Organization
Scalability and Resource Optimization
Reduce costs associated with hiring a full-time CISO. Get the services you need when you need them; scale them based on growth and evolving security needs.
Brand Protection
Identify and mitigate security risks to secure sensitive data. Implement early measures to thwart cyber-security incidents and protect the reputation of your business.
Real-Time Incident Response
Round-the-clock availability for urgent security concerns. Timely response to emerging threats. Tailored security plans and recommendations.
Compliance and Regulatory Alignment
Peace of mind your organization is complying with industry regulations and standards, and is getting assistance preparing for cybersecurity audits.
Vendor and Technology Assessment
Get insights into the security posture of third-party vendors and technologies to ensure they meet your organization’s security standards.
Security Awareness Training
Regular security training and phishing simulation programs for employees to promote a culture of cybersecurity awareness across the entire organization.
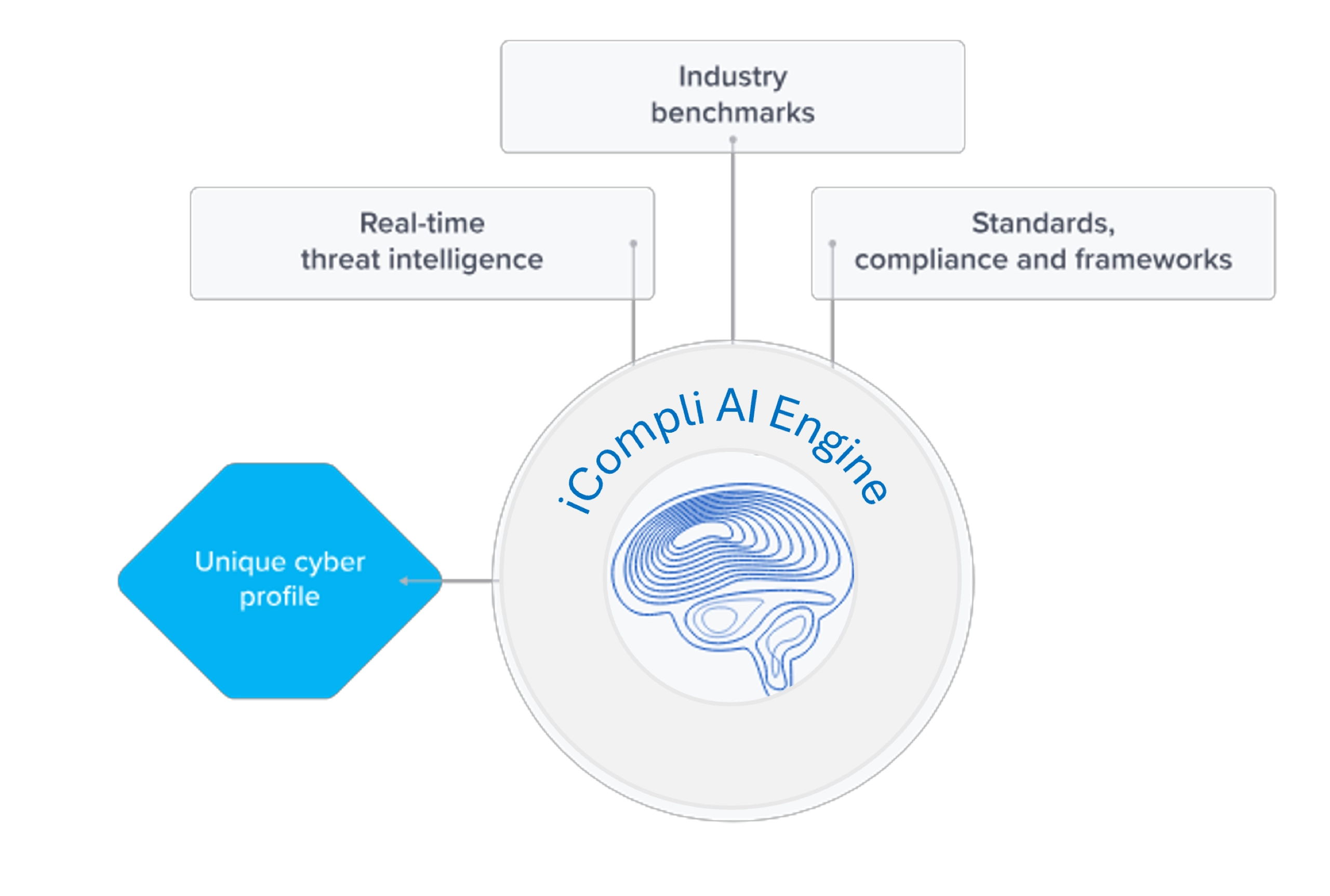
How the iCompli Platform Works
iCompli’s AI-driven platform is modeled after the expertise of the world’s best CISOs. iCompli provides you with automated risk and compliance assessments, auto-generated tailored policies, and actionable remediation plans with prioritized detailed tasks, task management tools, progress tracking and company leadership reports.
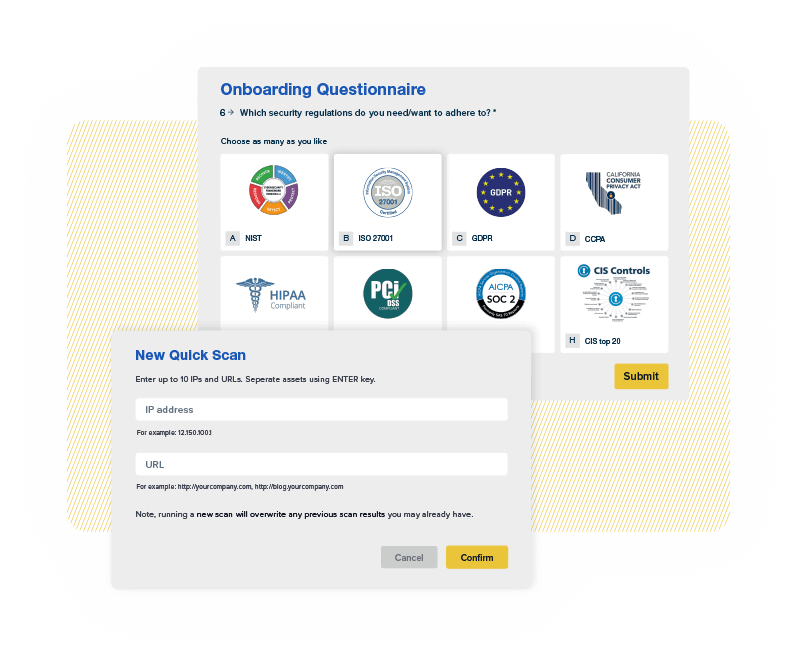
After an initial discovery questionnaire, we will automatically generate a self-guided, easy-to-follow questionnaire and express scan, to build your unique cyber profile.
Powered by proprietary AI algorithms, modeled after the world’s best CISOs, the iCompli engine continuously parses your organization’s cyber profile against relevant external resources like:
- The NIST Cybersecurity Framework;
- ISO 27001, CIS v8 frameworks and other standards;
- Industry benchmarks;
- External industry-based threat intelligence.
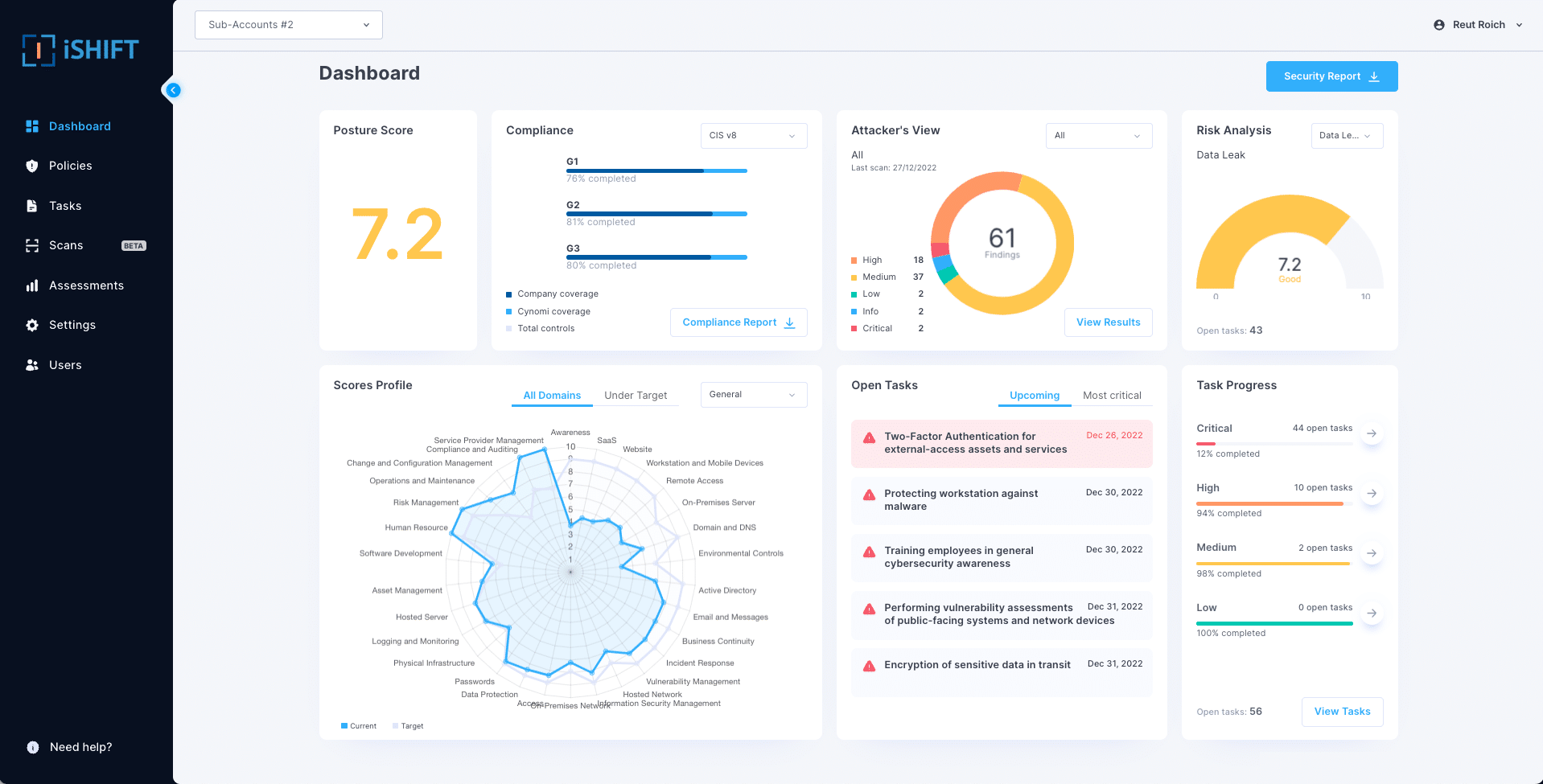
iCompli’s real-time cybersecurity posture dashboard includes gap analysis, compliance status, tailored and easy to follow policies, client-facing reports, and a customized remediation plan that includes prioritized, actionable tasks and the tools to manage their ongoing execution.
Supported Security Frameworks



- NIST-CSF
- NIST 800-53
- NIST 800-171
- NIST-SSDF
- FFIEC
- CIS V8
- ISO 2701 2013
- ISO 2701 2022
- SOC2
- CMMC Level 1
- CMMC Level 2
- HIPPA
- GDPR
- NIS 2 Directive
- PCI-DSS
- Cyber Essentials
- FTC Safeguard
- New SEC Regs
- ICS Cybersecurity
vCISO Expertise
Why Use Our Fractional CISO Service
Proven History implementing vCISO solutions and a team boasting prior roles as CISO, CTO, CIO, and CISSP certification
Executive-level Expertise for scalable and swift results
Security-First Approach to data protection, privacy, encryption, access controls, and security audits
Compliance-Driven Work to align your tech ecosystems with leading security standards
Comprehensive Security Partnership focused on experience, diligence, and regulatory compliance for your business protection
Recommended for You
Ready to Implement an Effective Information Security Program?
Crafting an Information Security Chain of Command: The Fine Balance between Accountability and...
iShift and Cynomi Provide Advice on Better Cybersecurity
As cyberthreats and compliance requirements escalate, it is critical for businesses to address...
iShift Insights – the Halloween Edition
Cybersecurity Awareness Month might be ending, but that doesn’t mean you should be hanging up your...